In today's world, where everything seems to be through a digital medium and as such making sure our identities stay safe and private is vital. When you think about it – anytime you use an online service, our digital footprint persists. From financial transactions to social engagements, the digital sphere has become an integral part of our daily routines.
As such, there is an immediate need for a robust, secure, and private system of identity verification. Conventional methods often result in exposing sensitive personal information and have proven vulnerable to data breaches and identity theft.
Enter Polygon ID, a breakthrough solution built on the principles of self-sovereign identity (SSI) and privacy.

What is Polygon ID?
Simply put, Polygon ID allows users to verify their identity without revealing any personal information about themselves. This ensures both the Freedom of Expression and Privacy by Default.
There are complex cryptographical systems called zero-knowledge proofs being used behind the scenes to secure the user's identity.
Core Concepts of Polygon ID
Decentralized Identifiers (DIDs): Each identity within the Polygon ID system is assigned a unique identifier known as a Decentralized Identifier (DID). This serves as a unique reference for an identity within the system.
Verifiable Credentials (VCs): Verifiable Credentials are pieces of information associated with an individual, organization, or entity. These could range from basic details like age to more complex credentials like membership certificates issued by a DAO. Every identity-based information is represented by a VC.
It can represent the same information a physical credential does. However, the addition of technologies, such as digital signatures, makes verifiable credentials more tamper-evident and more trustworthy than their physical counterparts.
VCs are cryptographically signed by the issuer.
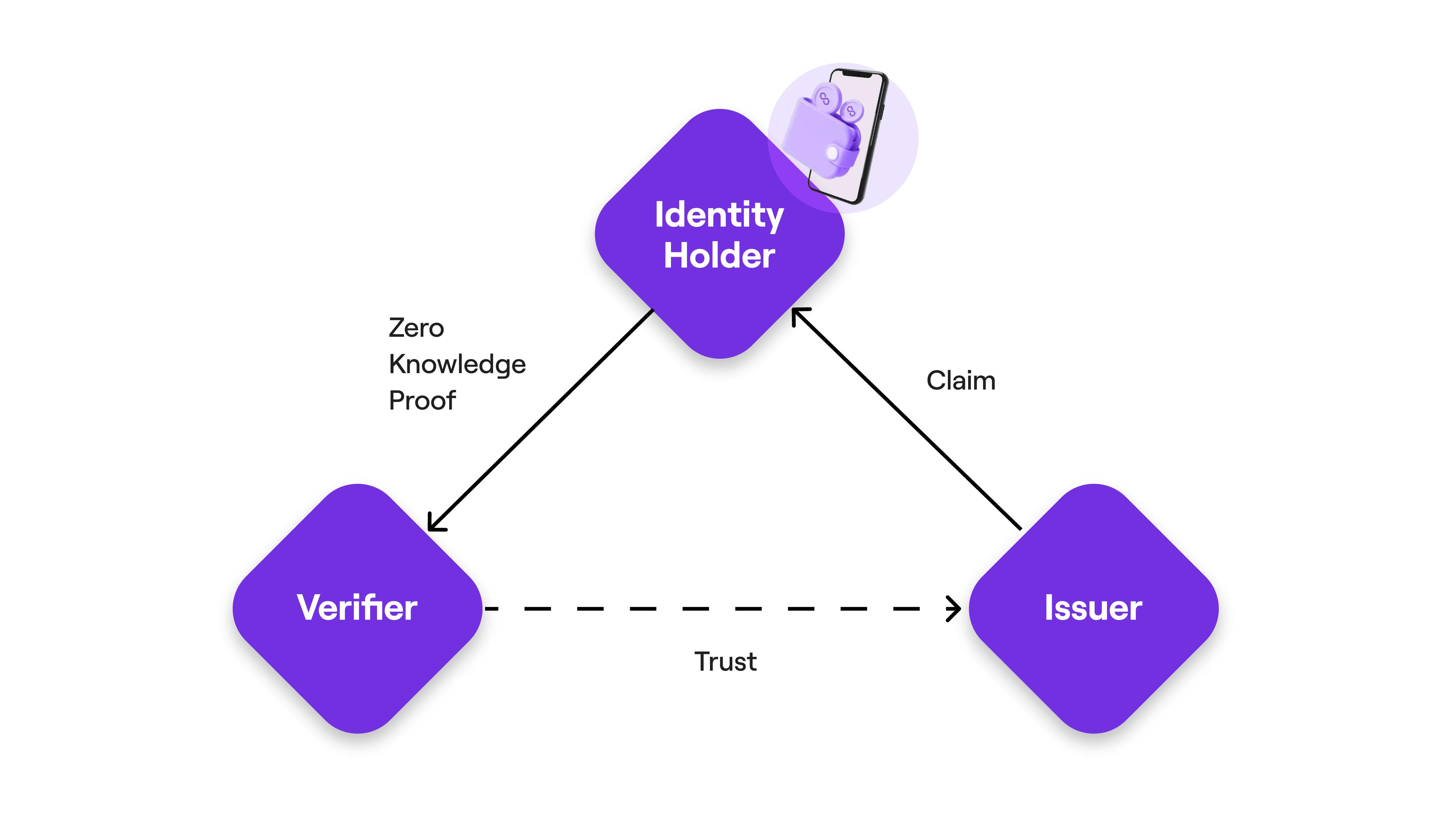
The architecture of Polygon ID consists of 3 entities (called the Triangle of Trust):
Identity Holder: An entity that holds claims in its wallet. A VC is issued by an Issuer to the Holder. The Identity Holder generates zero-knowledge proofs of the VCs issued and presents these proofs to the Verifier, who verifies that the proof is authentic and matches specific criteria.
Issuer: An entity (person, organization, or thing) that issues VCs to the Holders. VCs are cryptographically signed by the Issuer. Every VC comes from an Issuer.
Verifier: A Verifier verifies the proof presented by a Holder. It requests the Holder to send a proof based on the VCs they hold in their wallet. The Verifier then verifies the proof against specific criteria, ensuring its authenticity.
Let's understand with an example
Suppose a university wants to provide digitized course certificates to its graduate students. The certificate will hold the following details:
Name of the student
The year in which the student graduated
Course name
Honor or Merit status
Consider the scenario: The university follows the conventional method of converting the certificate to a PDF. If a student who has received this PDF wants to prove he is a graduated student(say at an alumni meet), he/she will need to show the entire PDF which contains extra details that may/may not be required to show(such as the course name/honor status). Hence, this becomes a breach of privacy.
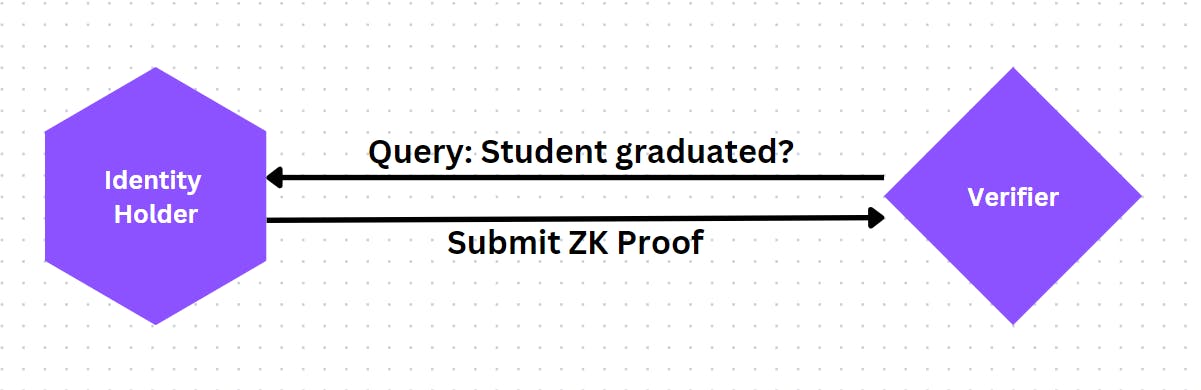
Here's where Polygon ID saves the day with its highly-secured zk-powered identity system. Here, the university will act as an Issuer and will be responsible for creating the Verifiable Credentials and assigning with to the respective students. The students in turn are the Identity Holders and hold the VCs generated by the university. If a student wishes to prove his graduation, all he needs to do is create a zk-proof of the VC and send it to the Verifier(say the alumni meeting security). The Verifier will run checks to see if the proof is valid. Hence, the student do not need to expose any details about their certificate.
The only detail the Verifier receives is: "Has the student graduated? Yes/No"
For another example, check out this tweet
The Issuer Node
As stated above, the Issuer is a source of information for any identity. The Issuer will generally run an Issuer Node(although there are other methods as well) which is a Docker container used to run a self-hosted server. This server provides certain APIs for the Issuer to run its functions. The APIs available for the Issuer are:
Create Private Key - API to generate a Private Key which creates a DID for the specific Issuer to authenticate their identity.
Create Credential - API to create and fill data in a Verifiable Credential.
Store Credential - API to store their credentials inside a database.
Communication - API to connect to an Identity Holder's wallet to send over the VC. This may be done through a QR code or hyperlink.
Revoke - API to revoke claims or cancel a VC.
The Verifier Role
A Verifier is any web2 or web3 platform that wants to authenticate users based on their Credentials.
Verifiers can set up queries based on users’ existing Credentials collected from a broad set of issuers. These queries set up the criteria for a valid proof such as "Has the student graduated?" or "Is the bank balance > $X?"
The Polygon team has created an exhaustive zk Query Language(ZQL) to help make this process easier.
The verification of the credential can happen both on-chain as well as off-chain.
For off-chain, the Verifier SDK provides the elements to create a customized Query, set up a verifier and generate a QR code on the client side to request proof from the user.
For on-chain, the Verifier SDK allows Dapps to verify users' credentials inside a Smart Contract using zero-knowledge proof cryptography.
Polygon ID Wallet app
The Polygon ID Wallet app is a reference implementation built using the Wallet SDK. It has a simple user interface and seamless UX to facilitate its main uses: managing credentials and generating proofs for verifiers. Learn more about the wallet here.
The app is available for Android and IOS:
For Android: Polygon ID on Google Play
For iOS: Polygon ID on the App Store
For a more comprehensive deep dive into the workings of Polygon ID, check out the official documentation
That's it for this post. I hope you have a better understanding of how Polygon ID is trying to secure the digital identity landscape.
For more informative posts, follow me on Twitter
Thank you for reading 🎉
